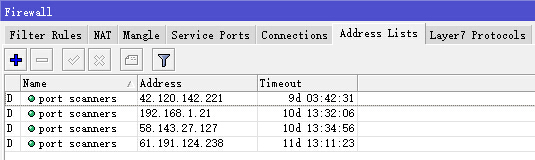
PS:如题,本脚本可防止外网黑客恶意扫描ROS设备,自动加入黑名单。
脚本如下:
/ip firewall filter add action=add-src-to-address-list address-list="port scanners" \ address-list-timeout=2w chain=input comment="port scanners to list " \ protocol=tcp psd=21,3s,3,1 add action=add-src-to-address-list address-list="port scanners" \ address-list-timeout=2w chain=input comment="NMAP FIN Stealth scan" \ protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg add action=add-src-to-address-list address-list="port scanners" \ address-list-timeout=2w chain=input comment="SYN/FIN scan" protocol=tcp \ tcp-flags=fin,syn add action=add-src-to-address-list address-list="port scanners" \ address-list-timeout=2w chain=input comment="SYN/RST scan" protocol=tcp \ tcp-flags=syn,rst add action=add-src-to-address-list address-list="port scanners" \ address-list-timeout=2w chain=input comment="FIN/PSH/URG scan" protocol=\ tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack add action=add-src-to-address-list address-list="port scanners" \ address-list-timeout=2w chain=input comment="ALL/ALL scan" protocol=tcp \ tcp-flags=fin,syn,rst,psh,ack,urg add action=add-src-to-address-list address-list="port scanners" \ address-list-timeout=2w chain=input comment="NMAP NULL scan" protocol=tcp \ tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg add action=drop chain=input comment="dropping port scanners" \ src-address-list="port scanners"
 Ros资源网
Ros资源网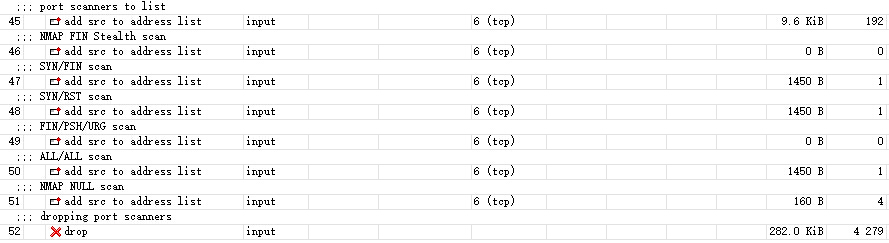
评论前必须登录!
注册